BRENDAN FLAHERTY, MBA
READ OUR PUBLICATIONS
We send monthly newsletters to our clients, colleagues, and interested parties.
The Evolution of Data Security

According to Eric Schmidt, we create as much information in two days now as we did from the dawn of man through 2003. The digital revolution has been powered by cheaper and faster infrastructure, allowing for the creation and storage of more data. More isn’t always better, but this treasure trove...
Cybercriminal Activity On The Rise Due To The Pandemic

To say that 2020 has been an eventful year is obviously an understatement. The ripples of COVID-19 have disrupted personal and professional lives across the United States and beyond. Social distancing measures forced companies and their employees to work from home, relying on mobile technology...
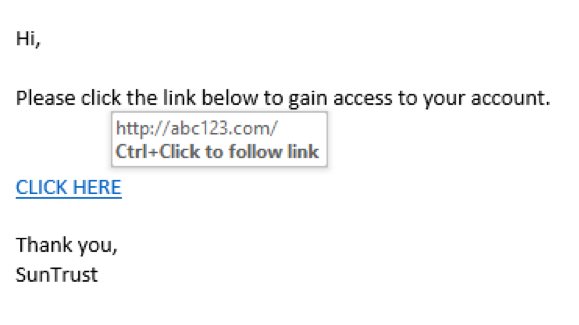
8 Ways to Protect Yourself From Phishing Scams

Every day, thousands of Americans fall victim to phishing scams. Phishing attempts by cybercriminals typically come in the form of email or text messages in order to trick unsuspecting individuals. Their goal is for the receiver to click a malicious link or attachment, or give away sensitive...
The Dangers of Public WiFi

At The Fiduciary Group, we proactively take a number of precautions every day, using a wide range of technology to minimize the risk of compromising client information. It’s important for our clients to exercise caution as well, particularly when using public WiFi. WiFi hotspots are popular,...
Cyber Security — Thoughts in Hindsight

Imagine your entire world being turned upside down. You thought it wouldn’t happen to you. But now your accounts have been hacked and you are exposed. For many, cyber security is an afterthought until it happens personally. Yet taking simple steps can greatly improve your chances of avoiding data...
Major Life Events

Being the helpless romantic and nerd that I am, I proposed to Lauren on Tax Day 2017. We grew up an hour apart in New Hampshire. We both attended UNH and met through mutual friends. When we graduated, Lauren pursued her career in nursing while I joined a startup fintech company. Since then, we’ve...
Indentity Theft
Most people have been, or know someone who has been, affected by identity theft. It happens to those in their 20’s, those in their 90’s, and to all ages in between. According to the Federal Trade Commission, identity theft occurs when someone uses personally identifying information (PII) without...
